- 04 Mar 2024
- 3 Minutes to read
- Print
- DarkLight
- PDF
Configuring SSO with ADFS
- Updated on 04 Mar 2024
- 3 Minutes to read
- Print
- DarkLight
- PDF
Business and Enterprise Scale only | |
Platform(s) | Web/Browser, Mac app, and Windows app |
Related reading |
Setting up SSO for ADFS
The admin panel is a centralized tool to help Airtable admins manage their organization. Learn how to set up SSO logins for your organization.
Step 1: Adding a “Relying Party” using the ADFS setup wizard
In the left navigation pane of ADFS, select Relying Party Trust, then Add Relying Party Trust, then Start.
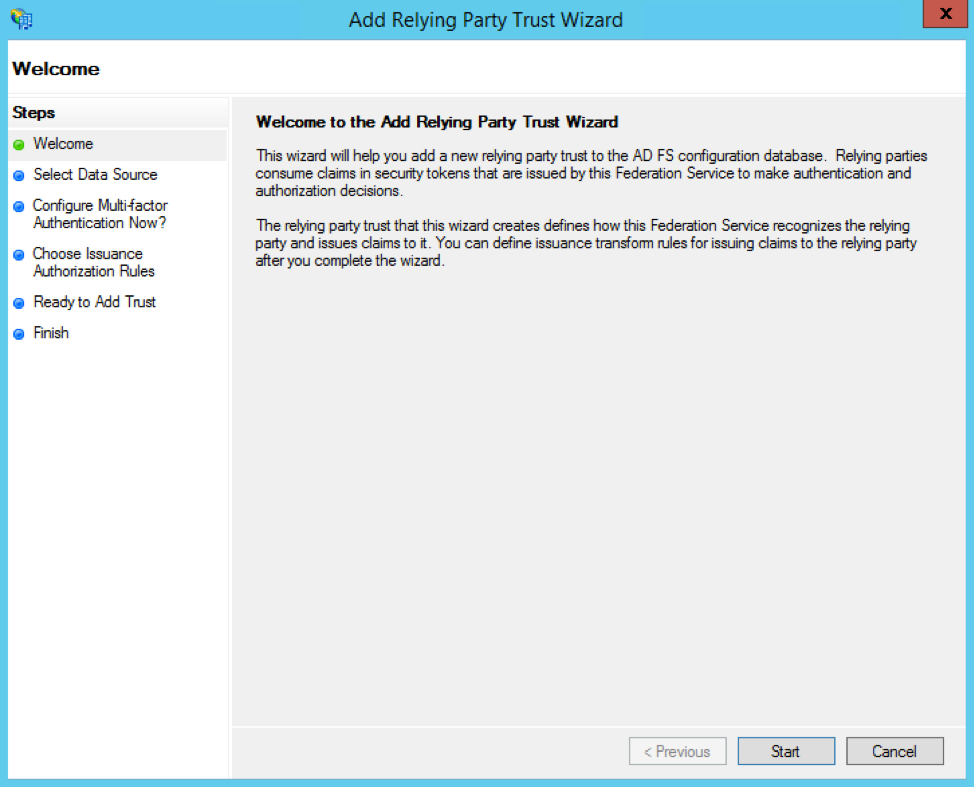
Click the radio button option to Enter data about the relying party manually, then click the Next button.
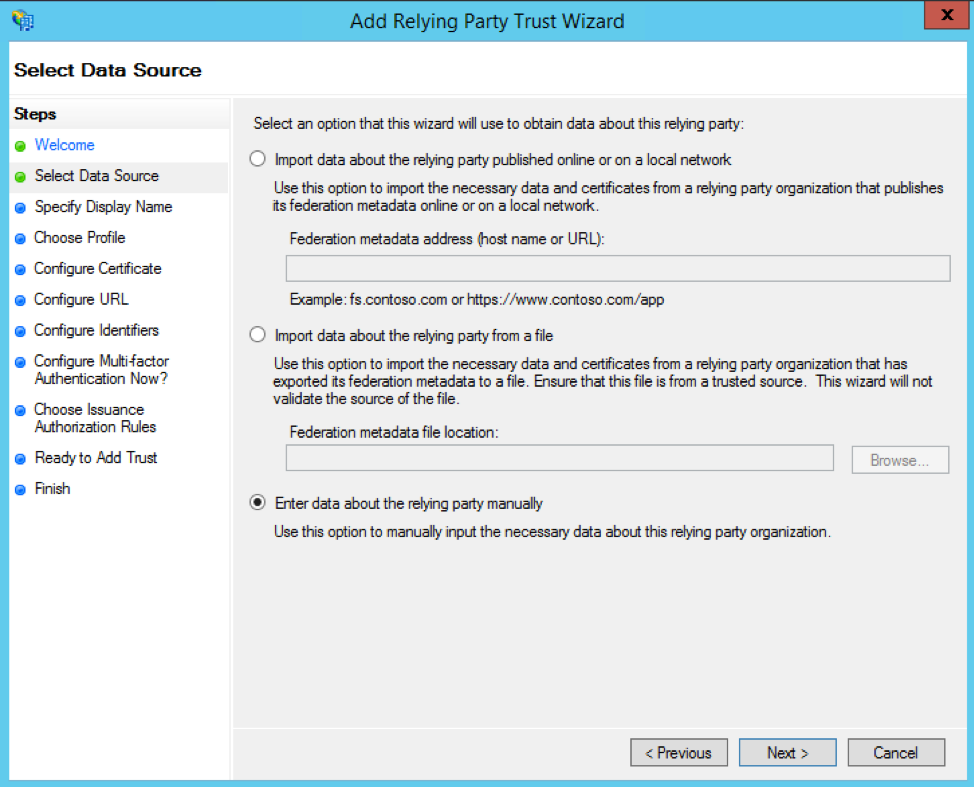
You can enter whatever display name you want (like "Airtable") and any optional notes—then click the Next button again.
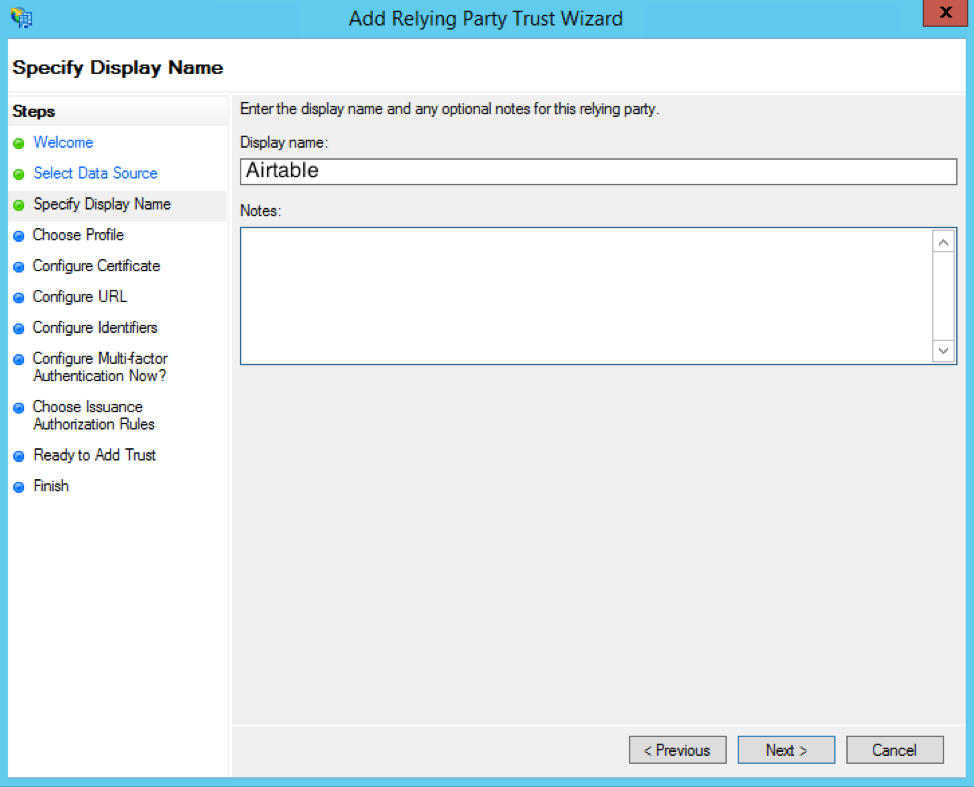
Next, pick ADFS profile as the configuration profile.
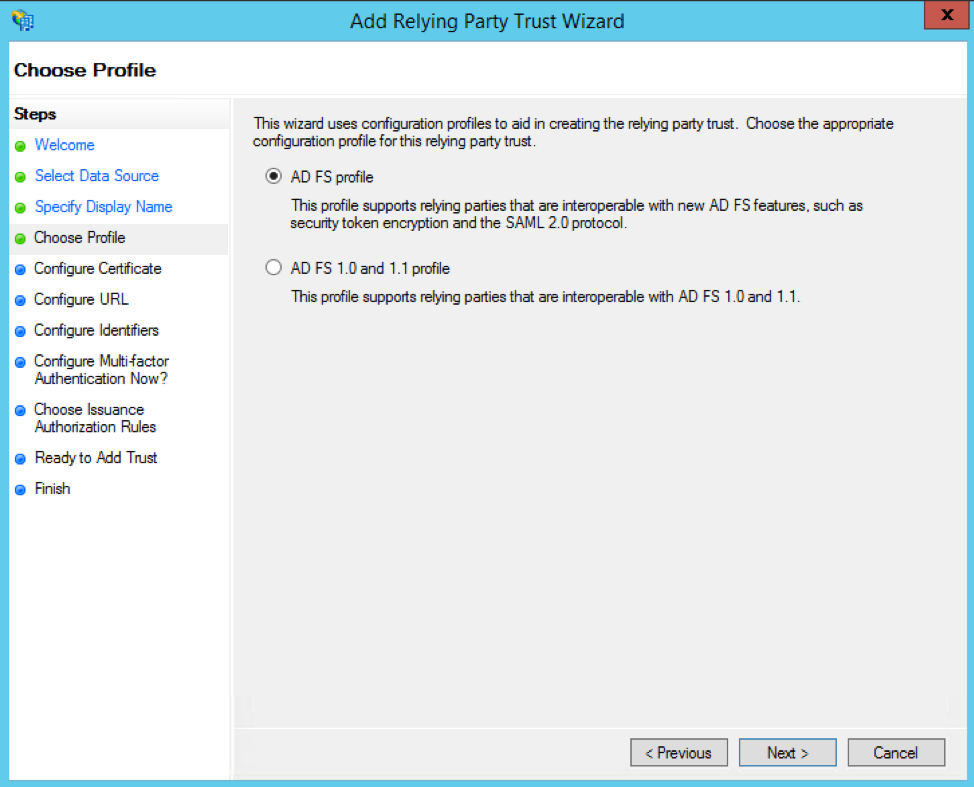
Click the Next button on the Configure Certificate page.
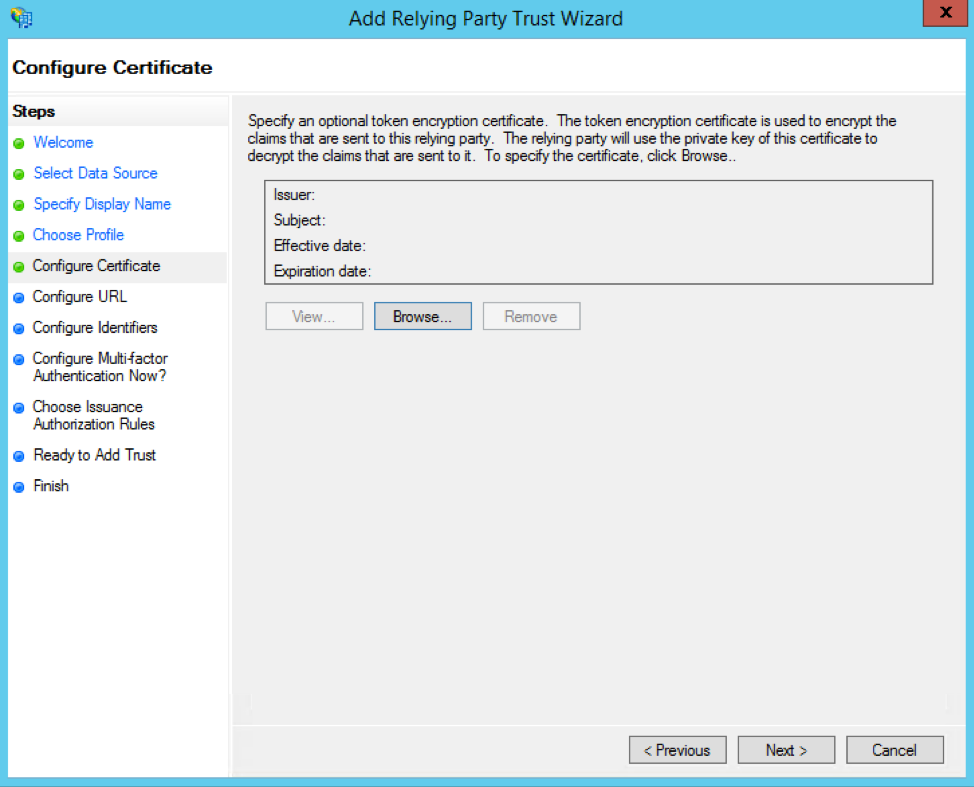
For the Configure URL page, check the Enable support for the SAML 2.0 WebSSO protocol box and paste in this URL:
https://airtable.com/auth/ssoCallback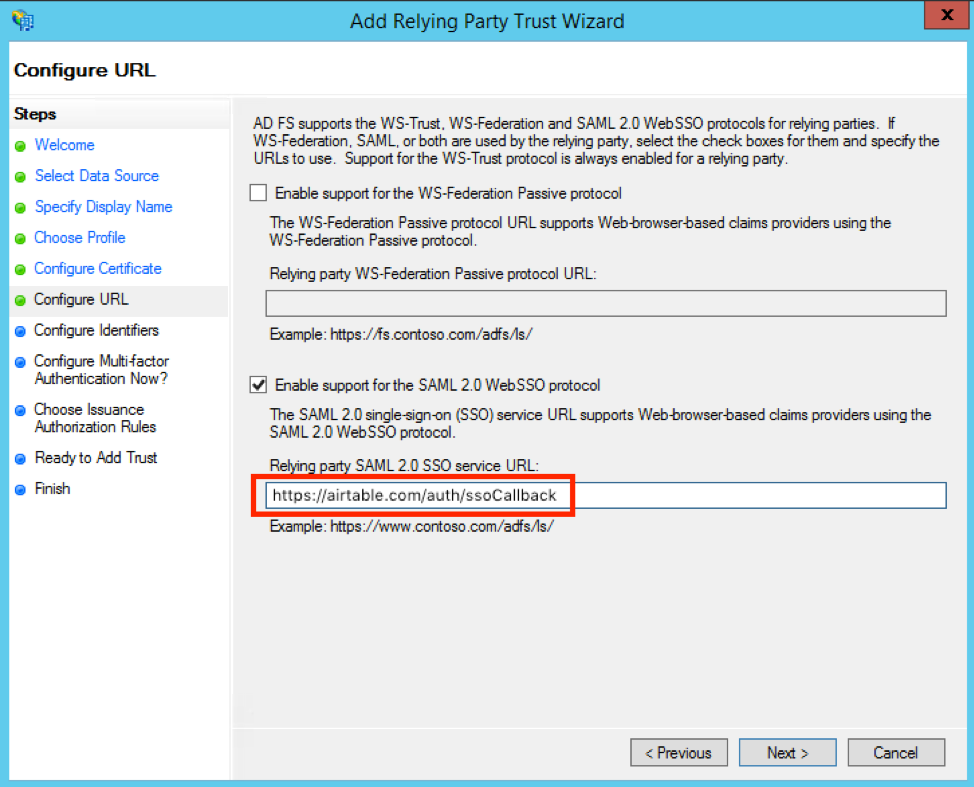
For the Configure Identifiers page, add https://airtable.com/sso/metadata0418.xml as a Relying party trust identifier.
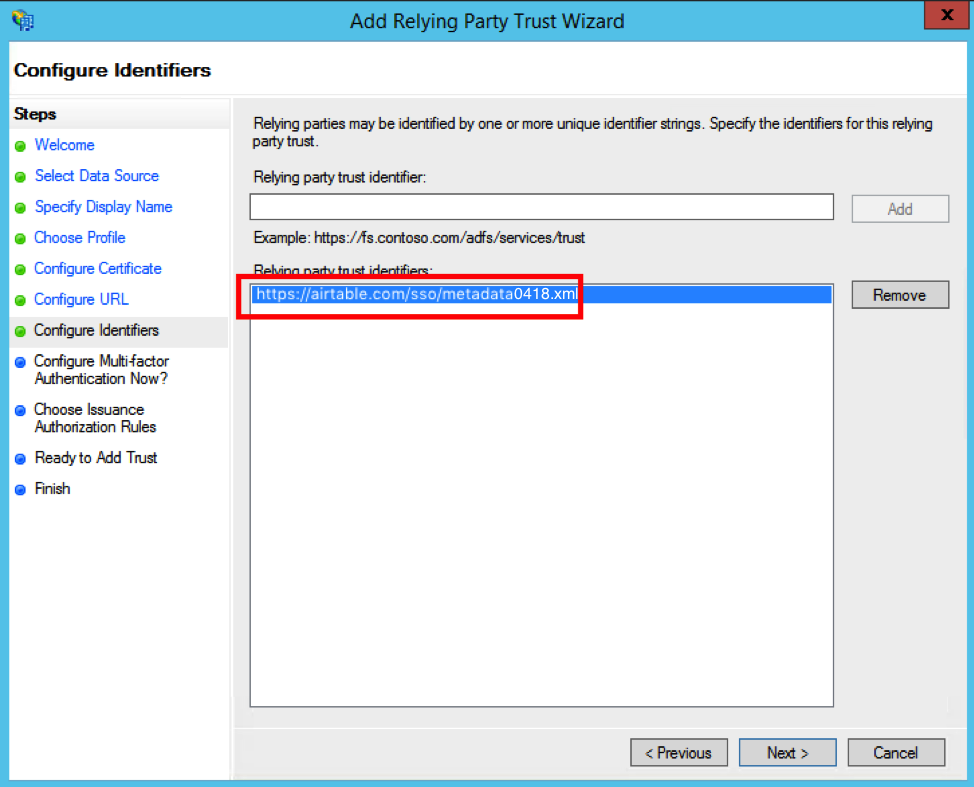
On the Configure Multi-factor Authentication Now? page, choose the "I do not want to configure multi-factor authentication settings for this relying party at this time." option.
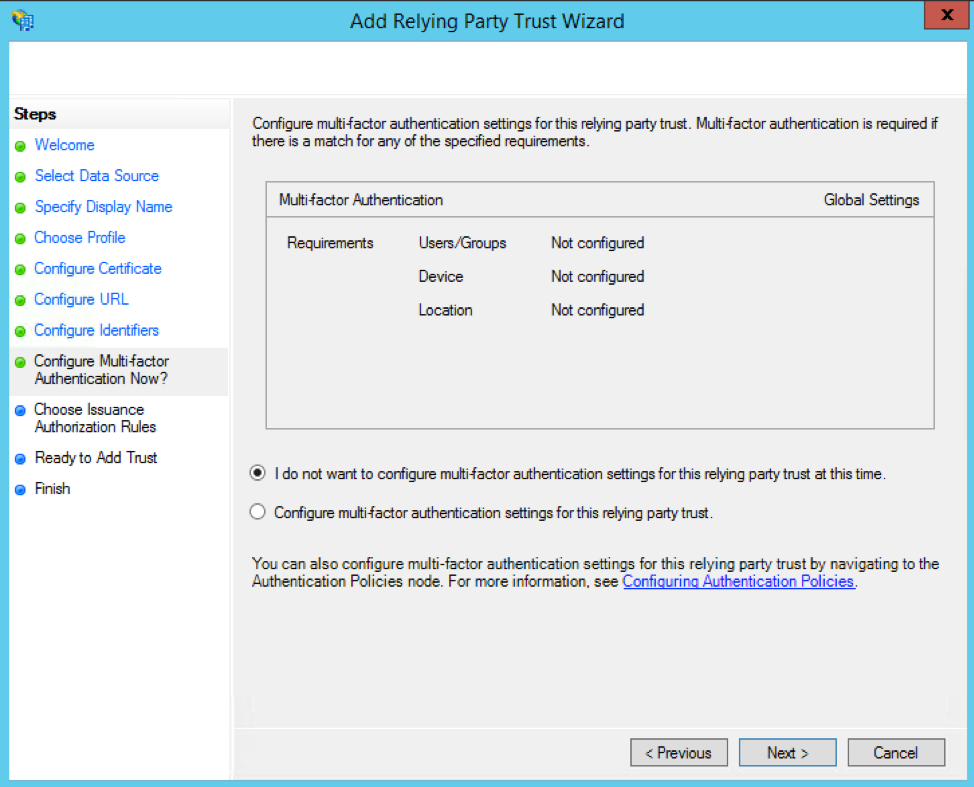
On the Choose Issuance Authorization Rules page, select the "Permit all users to access this relying party" option.
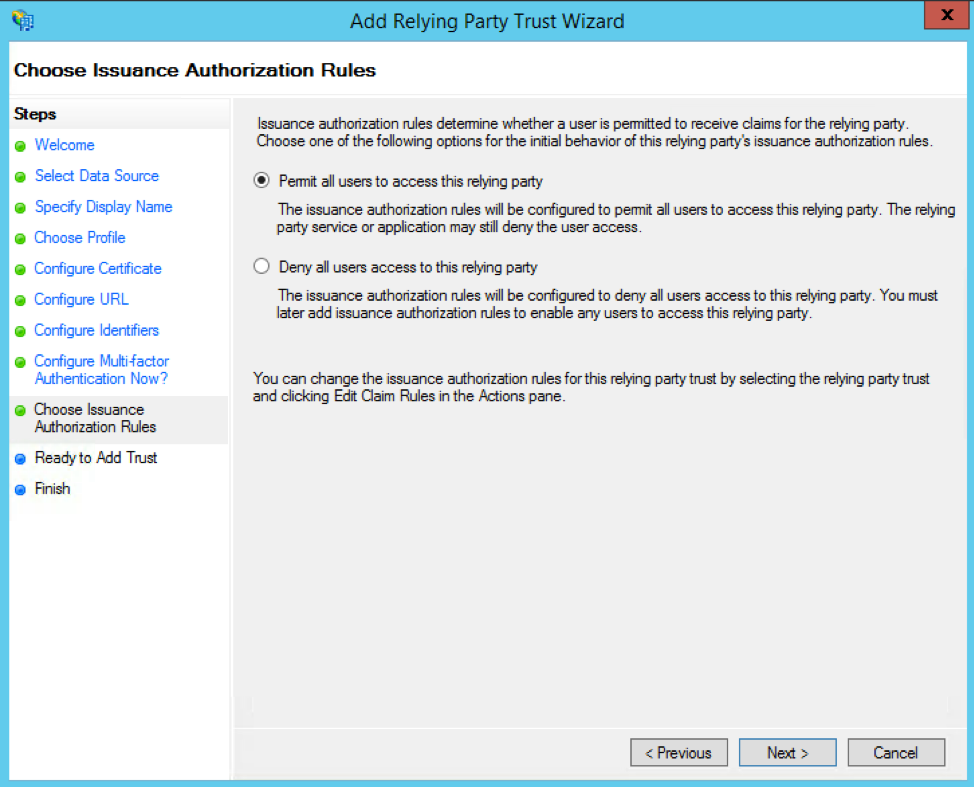
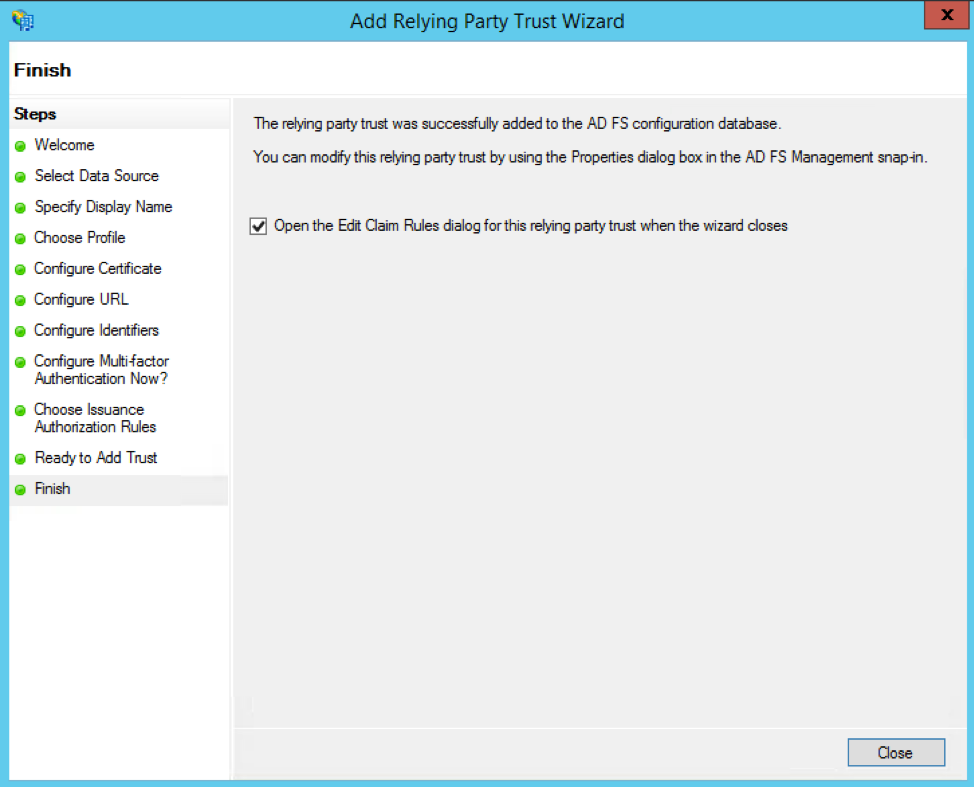
On the final screen of the wizard, check the "Open the Edit Claim Rules dialog for this relying party trust when the wizard closes" box. This will open the Edit Claim Rules dialog once you click the Close button.
Step 2: Adding a “Claim Rule” in ADFS
Once in the Edit Claim Rules dialog, go to the Issuance Transform Rules tab, then click the Add Rule button. This will open up the Add Transform Claim Rule Wizard.
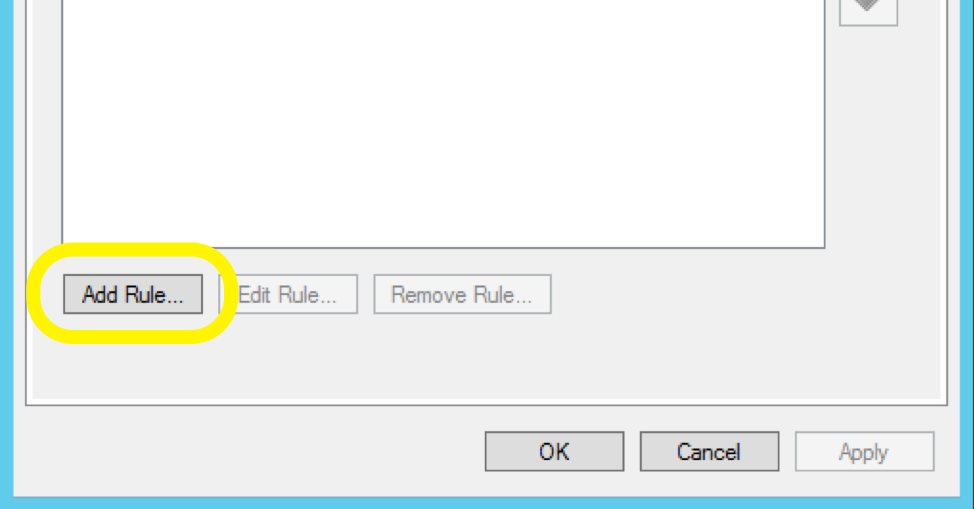
From within the Add Transform Claim Rule Wizard, you will be asked to Choose Rule Type. From the Claim rule template dropdown, select the Send LDAP Attributes as Claims option.
Give your claim rule a name (like "LDAP Email") and map the E-Mail-Addresses LDAP attribute in the left column to the E-Mail Address outgoing claim type in the right column.
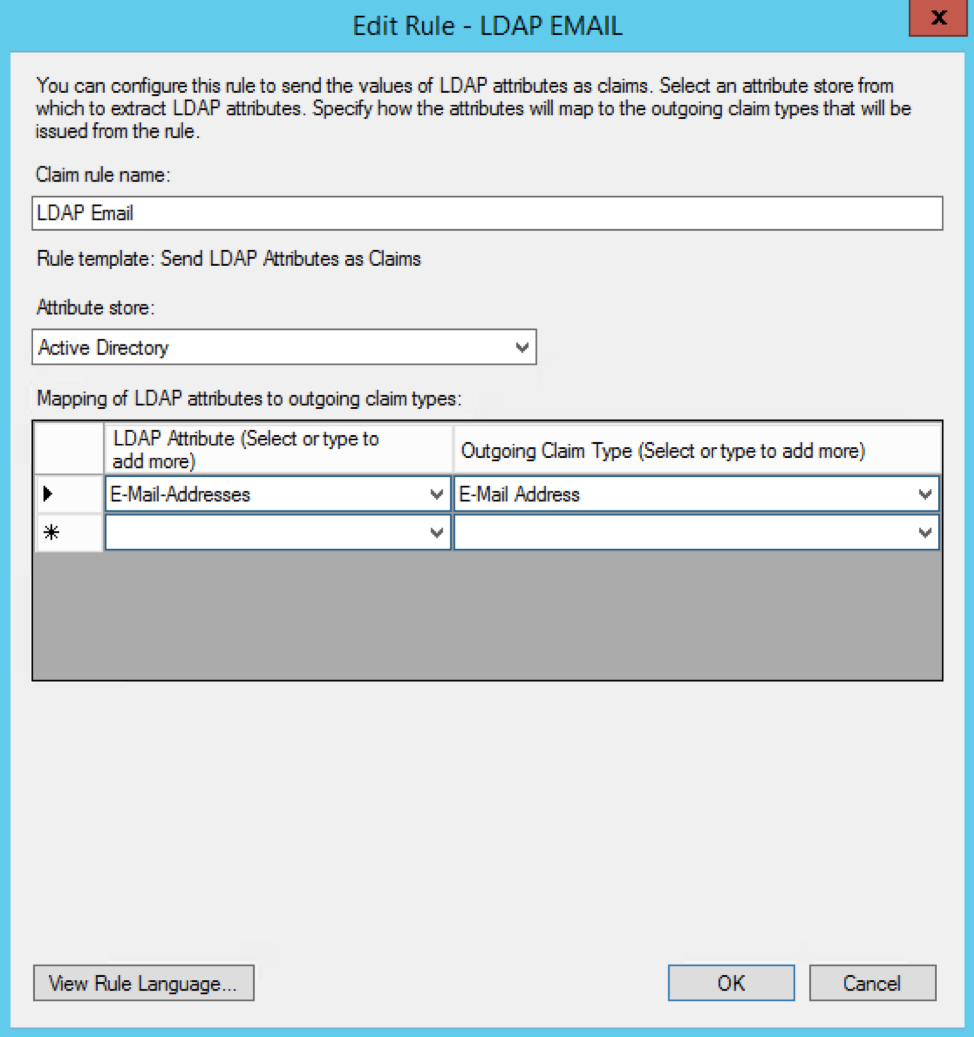
You'll need to add another Transform Claim Rule here. This time, select the Transform an Incoming Claim option from the Claim rule template dropdown.
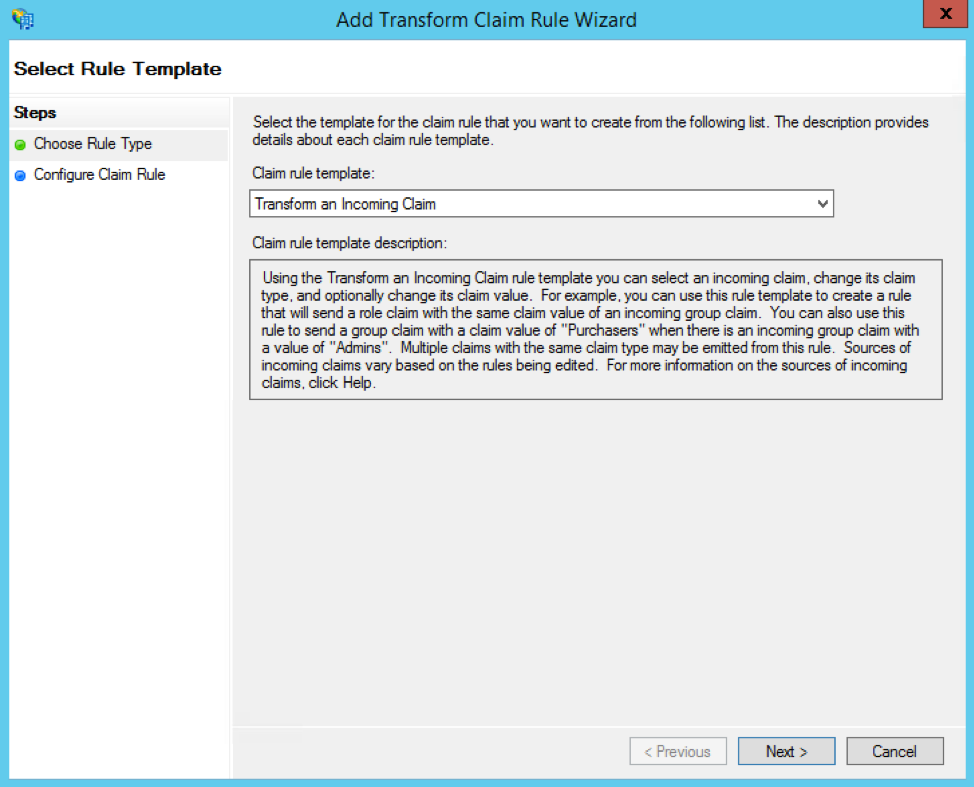
Give this claim rule a name (like "Email Transform"), then set the following values:
Set Incoming claim type to E-Mail Address
Set Outgoing claim type to Name ID
Set Outgoing name ID format to Email
Select the Pass through all claim values radio button
Airtable also supports the following additional attribute maps:
"urn:oid:2.5.4.4" -> Basic Information; Last Name
"urn:oid:2.5.4.42" -> Basic Information; First Name
When you're done, click the OK button to save this Claim rule, and OK again to exit the Transform Claim Rule Wizard.
Step 3: Editing Airtable’s relying trust properties in ADFS
Under the Advanced tab, select SHA-256 as the secure hash algorithm. Then, copy the following X.509 certificate and save it to something like airtable.crt:
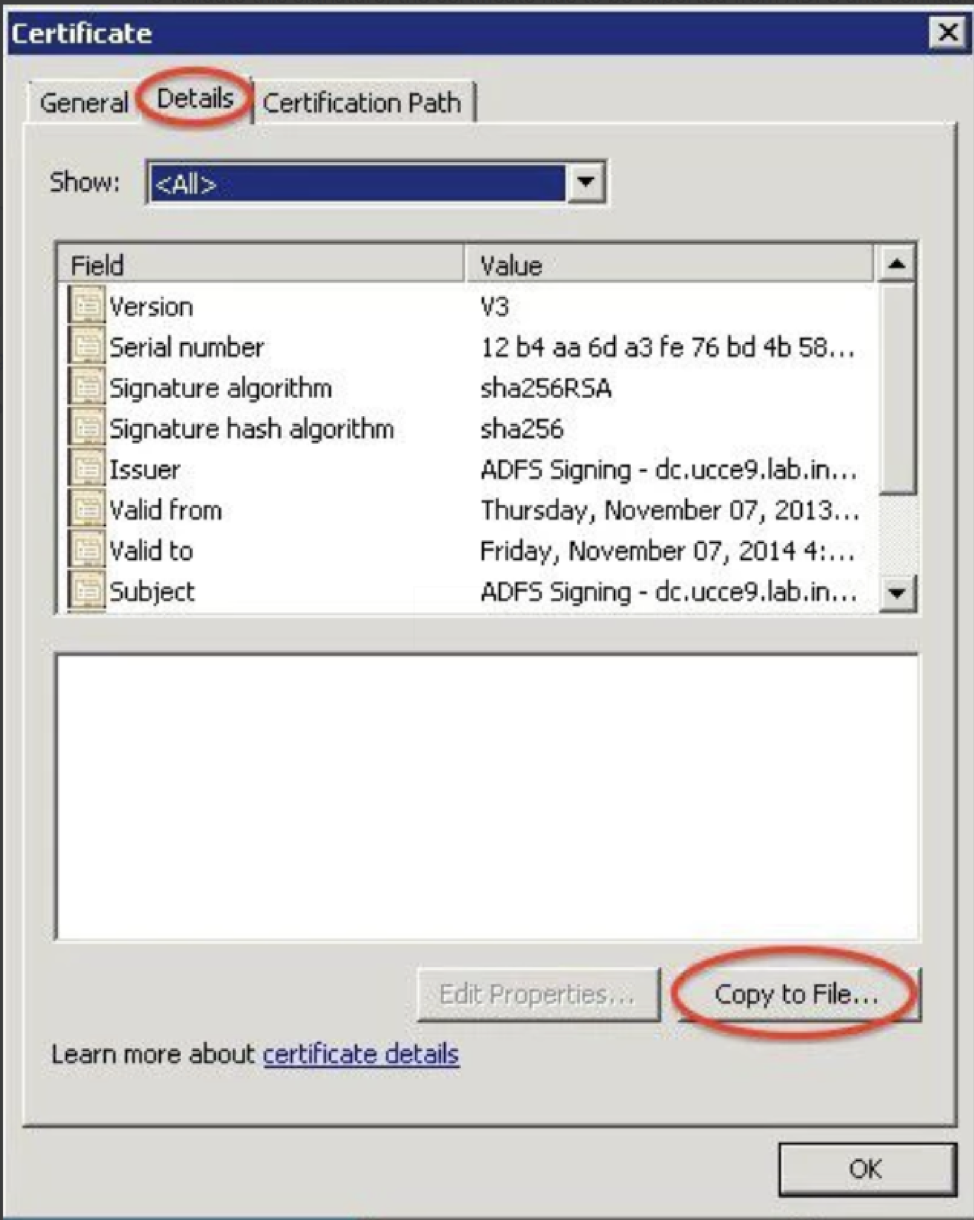
-----BEGIN CERTIFICATE----- MIIDUDCCAjgCCQDZhZQnLjon1zANBgkqhkiG9w0BAQsFADBqMQswCQYDVQQGEwJV UzELMAkGA1UECAwCQ0ExETAPBgNVBAoMCEFpcnRhYmxlMRUwEwYDVQQDDAxhaXJ0 YWJsZS5jb20xJDAiBgkqhkiG9w0BCQEWFXNlY3VyaXR5QGFpcnRhYmxlLmNvbTAe Fw0xODA0MjAyMzI1NTJaFw0zODAxMDEyMzI1NTJaMGoxCzAJBgNVBAYTAlVTMQsw CQYDVQQIDAJDQTERMA8GA1UECgwIQWlydGFibGUxFTATBgNVBAMMDGFpcnRhYmxl LmNvbTEkMCIGCSqGSIb3DQEJARYVc2VjdXJpdHlAYWlydGFibGUuY29tMIIBIjAN BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA3ORK7AMKzczh2JXWzKq4vI8jaHZ+ GcqNF6WHExEtPWrIN9Rpo/ogguZZ3BJs6dtUkPAt5M722BkJUggMFj9LREK8Vcl/ +3ffXJUhcIcatpXsq3iQE9Otbc5aFxSt6FKg410snTeI+VVYJ3cOgOQzO1ZEBjj8 DA1iB0w9ICd9DRj3LXa9S55B1q9TRPJwicbT9SwMJlF/VqSilS+QhDqhPiSrja7X WipQN3y0HwhqNlC3oPlBewjvyTLrmR6IGstxm01Wxj2JbHkGA9MgZKCMV5sQgA68 2DoIvbhDPOA/E5vjL5JwsyU/LjDhm0cfX6RiZ/OywGbs+KawLe29As+V9wIDAQAB MA0GCSqGSIb3DQEBCwUAA4IBAQC/ewo5+TeEGOnT6ko0X1C+Yduiu1IqXZc8Zw6w +9k06hg9IbO7u9VCevbKI/CwG4Il/6URGwqKKmU3kyUNsRmdsFMHWWrzeCPqa+94 FbRiaTjZcoV3I5++CjObWJgatIC9MLTxVKnQaGDSTk+dxwXOIANZ+iCh3SKQTRM+ r0YZUSIM+5hXWccsdnPtp+2GczzbUJ0rCWA/iQ0OwZrWpU0/XPnzjQguVrdIPDIh 3xPeT40txEg+mHAajGFfh6XhV86P8185fZ8R6G+gehqfByToNiCbb0BqipOaA+ej SDYXqYh7jx3D6X/gV9MnyGBVRy1t6COzk+OZDosPhkTFgclt -----END CERTIFICATE-----Under the Signature tab, click Add, then upload airtable.crt. Click OK to complete. Next, you'll need to export your token signing certificate. In ADFS, click the Certificates folder, then Token Signing certificate.
Click the Details tab, then click the Copy to File button.
Next, export as a Base-64 encoded X.509 (.CER) file.
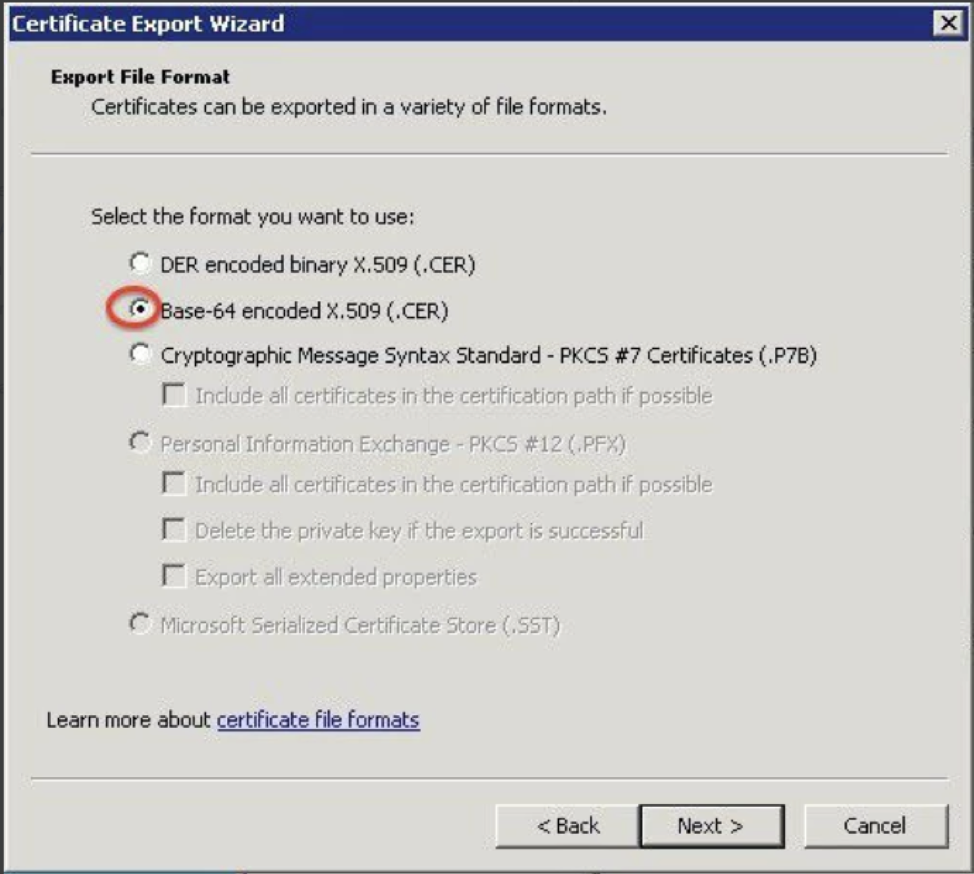
After that, submit your sign on URL and x.509 certificate (you can open the .cer file in a text editor and copy-paste it in) following the steps in this article.
After you have completed all of the steps, you should be able to log in from https://airtable.com/sso/login.
Troubleshooting
If you encounter any issues or need additional assistance, please contact us. If there are any relevant ADFS logs (Control Panel -> Administrative Tools -> Event Viewer -> Applications and Services Logs -> AD FS -> Admin), please include them in your email.
FAQs
If another team in my company already uses SSO with Airtable, how does this impact my Business or Enterprise Scale account?
In Airtable, our system expects Enterprise Scale accounts using shared domains—domains federated to multiple Enterprise accounts—to use the same SAML metadata for SSO. What this means is that if your company has existing Enterprise ScALE accounts with SSO configured, you will need to coordinate with the admins (or IT department) of the other accounts to obtain the current sign-in URLs, x.509 certificates, and ensure that your users have the necessary access to the Airtable tenant present in your company’s identity provider.
You can configure separate tenants or identity providers for domains unique to Enterprise Scale accounts, as each domain can be configured with its own SAML metadata.

















