Plan availability | Enterprise Scale only |
Admin | Admins |
Platform(s) | Web/Browser, Mac app, and Windows app |
Enterprise Key Management access and control
Enterprise Key Management (EKM) allows admins on the Enterprise Scale plan control over the data their users store in Airtable while also giving visibility into how those users access data.
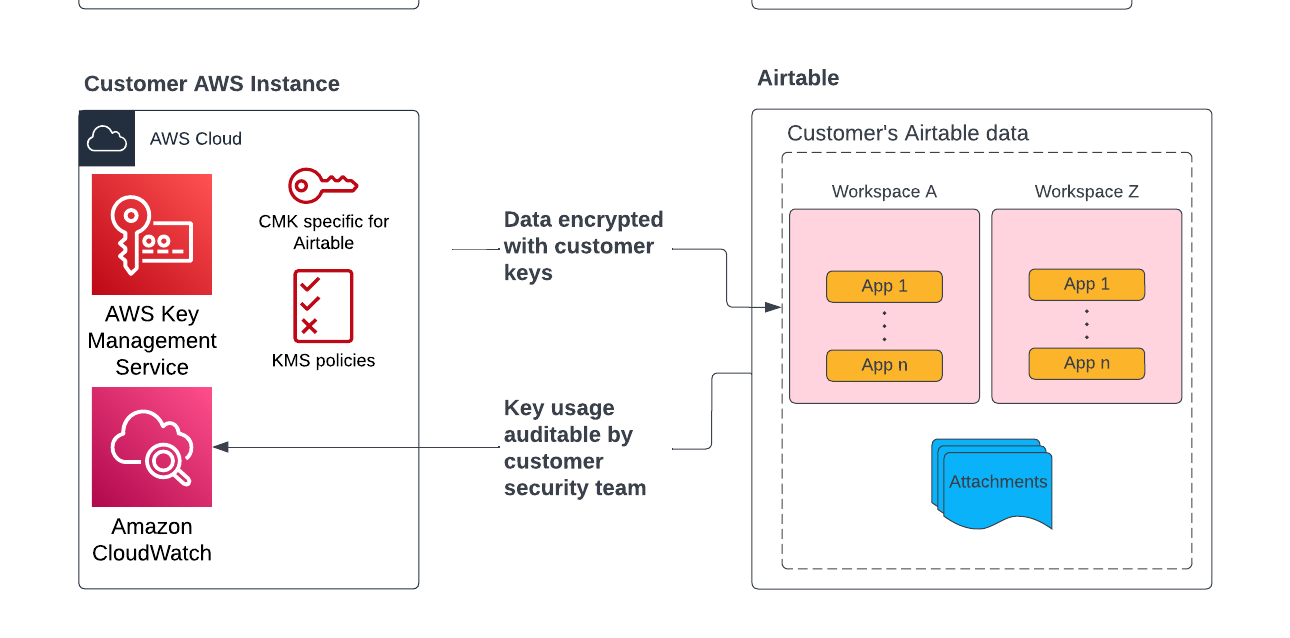
By default, Airtable encrypts data stored at rest using AES-256. EKM will now allow you to encrypt your organization’s applications using keys you own and manage through Amazon’s Key Management Service. You will also have visibility into the usage of those keys via AWS CloudWatch and CloudTrail.
By configuring different KMS policies, admins can manage and revoke key access on the application, workspace, and organization level. For example, you can use EKM to revoke access to a specific application while allowing collaborators to continue using other applications uninterrupted.
Configuring Enterprise Key Management in Airtable
Note
Once enabled, EKM cannot be disabled. We recommended existing customers with multiple enterprise accounts move to Enterprise Hub before enabling EKM.
To use EKM, you must configure a customer-managed key (CMK) in Amazon Web Services (AWS), which will be used across all your enterprise Airtable accounts. You will then create KMS policies that grant Airtable permission to use keys stored in your organization’s KMS to encrypt Airtable data (further details in our Implementation Guide).
After enabling EKM, all new applications will automatically be encrypted using your organization’s keys.
Existing applications will need to go through a migration process.
Depending on the amount of data your organization stores in Airtable, migration to re-encrypt existing application data with customer keys can take between 1-2 months.
Data encrypted by CMKs
The following data is encrypted with customer-controlled keys once EKM is enabled:
In-base data (record contents, comments, etc.)
Application and interface metadata (names and descriptions)
Attachments
Historical data (snapshots and record history)
Change event logs
Audit logs
Data encrypted with Airtable keys
The following data may continue to be encrypted with Airtable-owned keys:
User and team metadata (usernames, group names)
Data used for running the service (sanitized logs, etc.)
Airtable Sync integration: Emailed data (emailed files may be encrypted with Airtable keys for up to 30 days)
Airtable Automation trigger: Emailed trigger (emailed files may be encrypted with Airtable keys for up to 1 day)
FAQs
How can I get additional information or support setting up EKM?
For questions or support in setting up Airtable EKM, please contact your Airtable account representative or CSM.
My organization uses EKM and I’m unable to move bases between org units, what might be occurring?
When this occurs, you’ll likely encounter an error stating that only super admins can perform this action. Additionally, if you previously were able to move bases between org units, then this typically indicates a change in your permissions/security settings.
Ultimately, only super admins can move a base with EKM enabled between org units within the same enterprise. You’ll need to contact a super admin at your organization and either ask them move the bases or ask them to grant you super admin permissions.